by Eli Greenberg
One way or another, a process-driven approach can help companies better protect their information and the information of others over the short or long term. This relates to information such as PHI (Protected Health Information) and PII (Personal Identifiable Information) and cyber security and its many rules to combat hacks and stealing of private information.
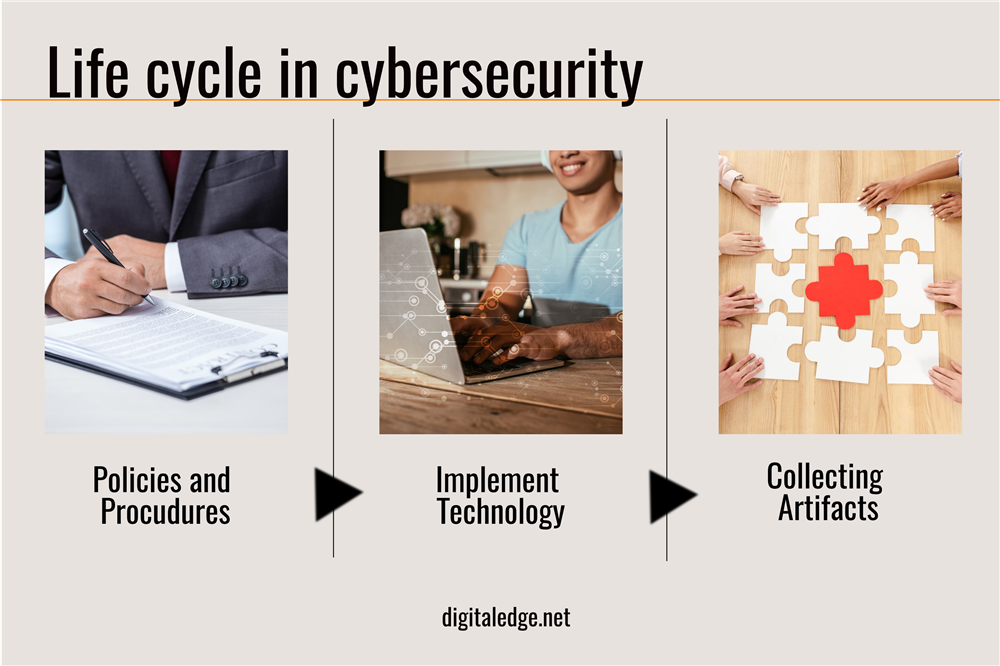
Such a process includes the following: collecting artifacts, implementing technology, and certain policies and procedures. These processes all play a role in preventing cyber security attacks. For example, collecting artifacts deals with tracking different footprints so a particular company can monitor who’s trying to steal from them.
In addition, implementing technology input networks, servers, and hardware will monitor the company’s most valued information.
Lastly, certain policies and procedures are a prudent process, and consider reviewing and checking that all of the private information is safe and has been saved successfully within the company’s network.
Digital Edge has a similar stance on how to prevent breaches from happening. Even we deal with this matter daily and have the resources to prevent it from happening.
We are always willing to help, so you can give us a call or visit our website: 800 - 714 - 5143 https://www.digitaledge.net/.
Even though companies are usually trying to prevent cybersecurity attacks, different places such as the US and EU have different policies to stop them. For example, the Gramm-Leach-Bliley Act was put in place by Congress and protects PII. This act handles financial institutions, which means that companies offering customers financial products or loans need to explain their information-sharing practices to their customers and safeguard sensitive data. This act even has enforcement from the FTC and SEC.
Another act, called the Sarbanes-Oxley act of 2002, is another example of how the US handles cyber security. Unlike the Gramm-Leach-Bliley Act, this deals with federal law that created auditing and financial regulations for public companies. Certain lawmakers established the legislation to help protect shareholders and employees with the public from accounting errors and fraudulent financial practices. This also has enforcement of the SEC.
In addition to many acts enacted by the US, The New York State “SHIELD” (Stop hacks and improve electronic data security), is a new law enacted by the NYS legislature. This law has a data security section and a data breach notification section. The data security section states that a person or business that owns or licenses computerized data that includes private information of a resident NY shall maintain safeguards to protect the security, confidentiality, and integrity of said private information.
The data breach notification section states that in the case of a data breach, the person who found the breach should notify the supervisory authority of the personal or company-wide data breach no later than 72 hours. CalCPA is another newer state law like the SHIELD law, but more about privacy rights.
This more recent law protects citizens’ private information and has private cyber security lawsuits under the “common law.” The “common law” is essentially judge-made law. The common law causes action for cyber security purposes, which include: negligence, negligent misrepresentation, breach of contract, breach of an implied warranty, invasion of privacy, and unjust enrichment.
Now, in the EU, cybersecurity is handled a little bit differently. The EU views privacy as a fundamental right. For example, the GDPR (General Data Protection Regulation) is a legal framework that puts guidelines for collecting and processing personal information from individuals who live in the EU. This framework also has a procedure that requires security controls, breach notification, and privacy rights.
Finally, when an individual in the EU finds or notices a breach, they must notify the government about any breaches within a couple of days. All these procedures, processes, and laws attempt to prevent hacks from occurring within a company.
Needless to say, it is not always successful, but it makes it harder for these breaches to accomplish their end goal of stealing private information.