Hackers improve techniques for tricking people into completing actions that penetrate their system. Users should remember that ANY attachments are potentially dangerous.
We always recommend using virustotal.com to verify attachments before opening them.
Here are a few new techniques used by hackers in recent incidents.
- Some malicious software can be hidden in your systems, monitoring your email conversations. It would interject your thread, posing as an email from one of the recipients and would have an attachment. The fact that this malicious email with the attachment came in the middle of conversation may trick some users in opening it.
- Some malware uses a template to tell users that the document was created on iOS and cannot be viewed properly unless the "Enable Content" button is clicked to force a user to enable the macros.
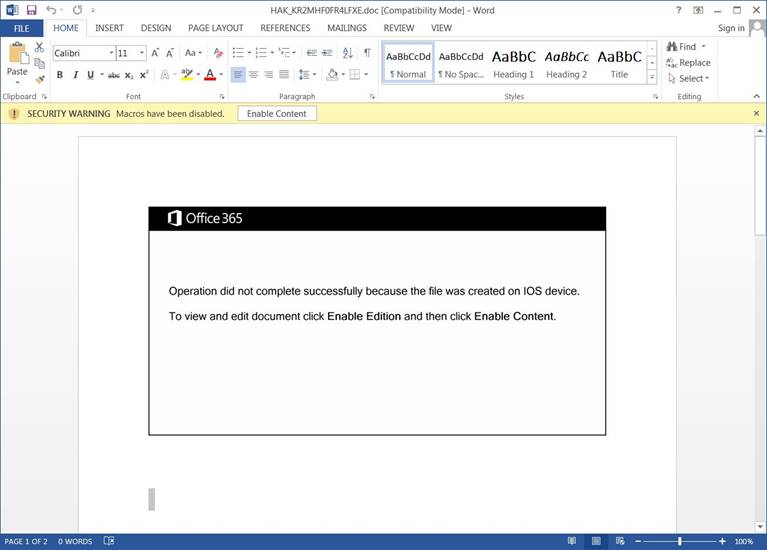
In this time of ever-evolving technology, it is crucial to stay vigilant. Digital Edge's cybersecurity team specializes in ways to stay protected and is always keeping track of the new techniques hackers come up with to try to infiltrate users.
Contact us if you have any questions or need support.